This is a MetaCTF CyberGames 2021 test that required forensic analysis of a .NET memory dump. Conducting such an examination may be unfamiliar to many, so I hope this article will be useful.
In this task, we took over the collection of intercepted packets and a dump of the process offered to you for consideration of the beacon.
In order to provide our leadership with the necessary clarity, we want to know specifically what actions the attackers took on this high-value machine (keep in mind - this is where the dump/captured packets are different from all previous tasks). Therefore, to recreate the picture of what happened, you will need to match the information in the intercepted packets and extract the necessary critical data from the memory dump.
First, let's look at packet capture with wireshark to understand what we are dealing with.
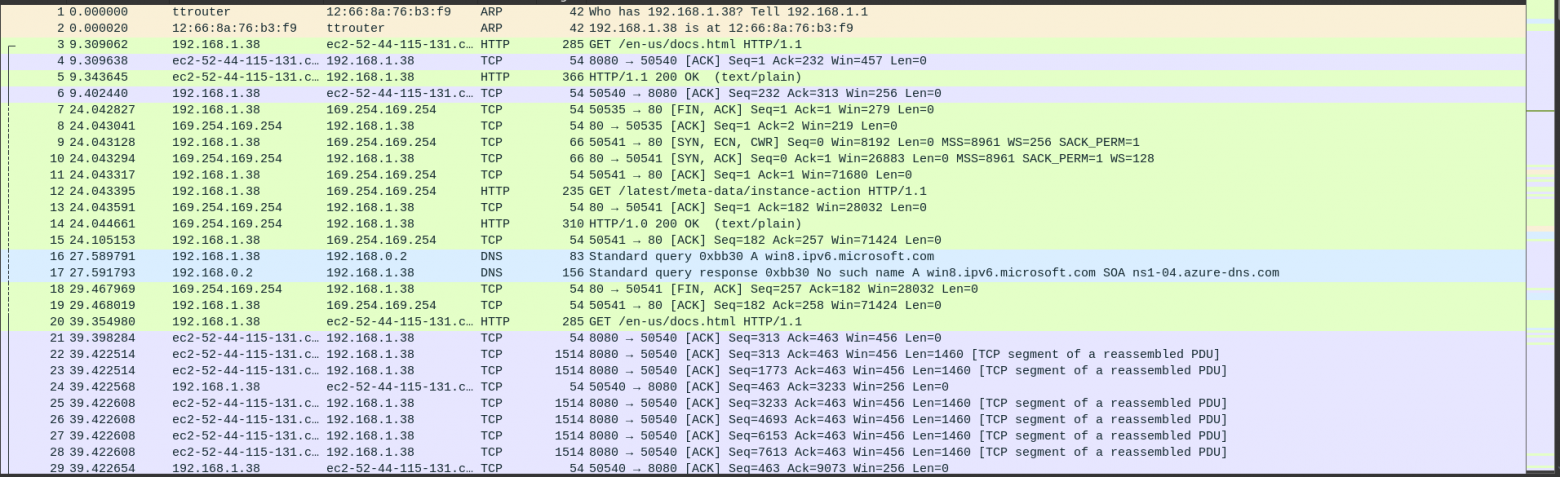
Here I immediately notice two packages of interest to us:
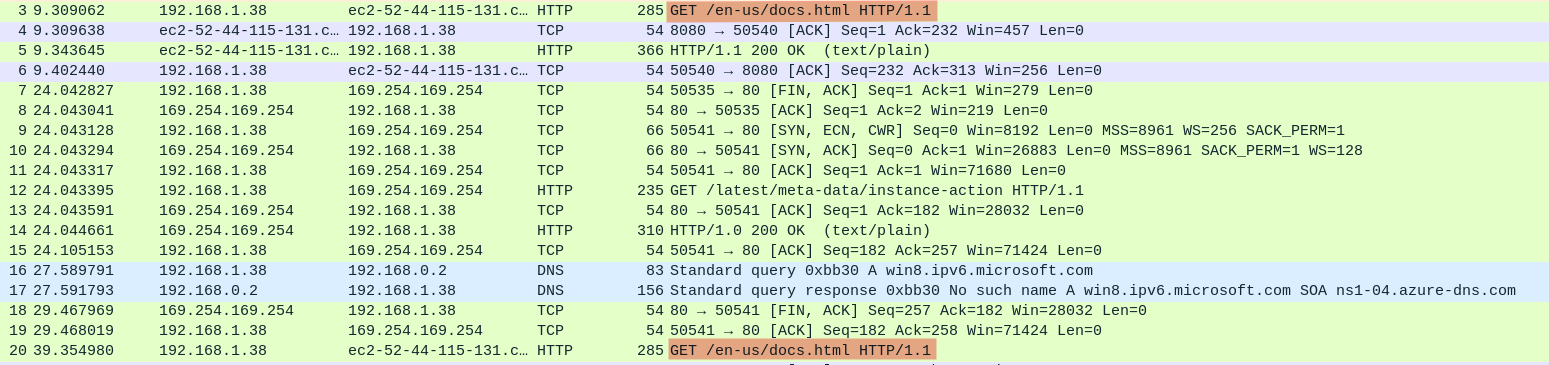
GET /en-us/docs.htmlis of interest because immediately after we observe the sending of a large amount of data. That being said, I don't attach importance GET /latest/meta-data/instance-actionto , since it's something about an EC2 AWS server that was left behind by accident.
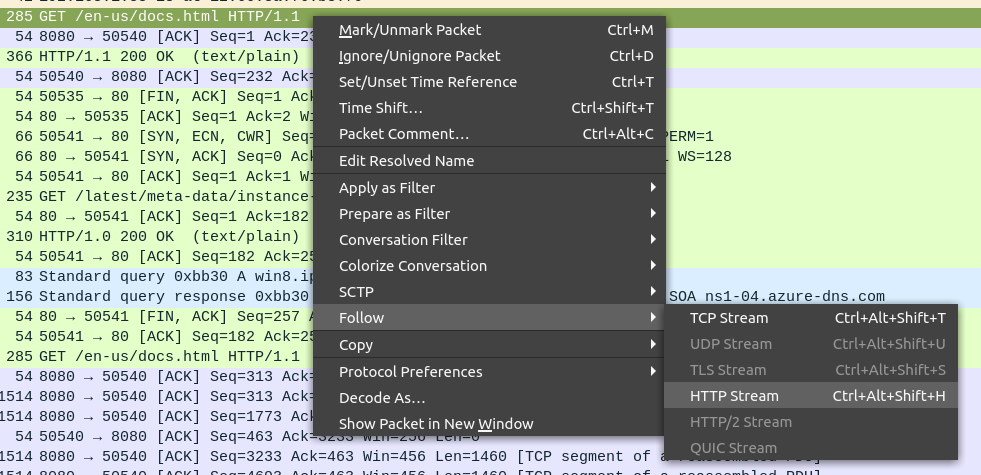
To see how the packages in question are involved in the entire session, use follow http stream.
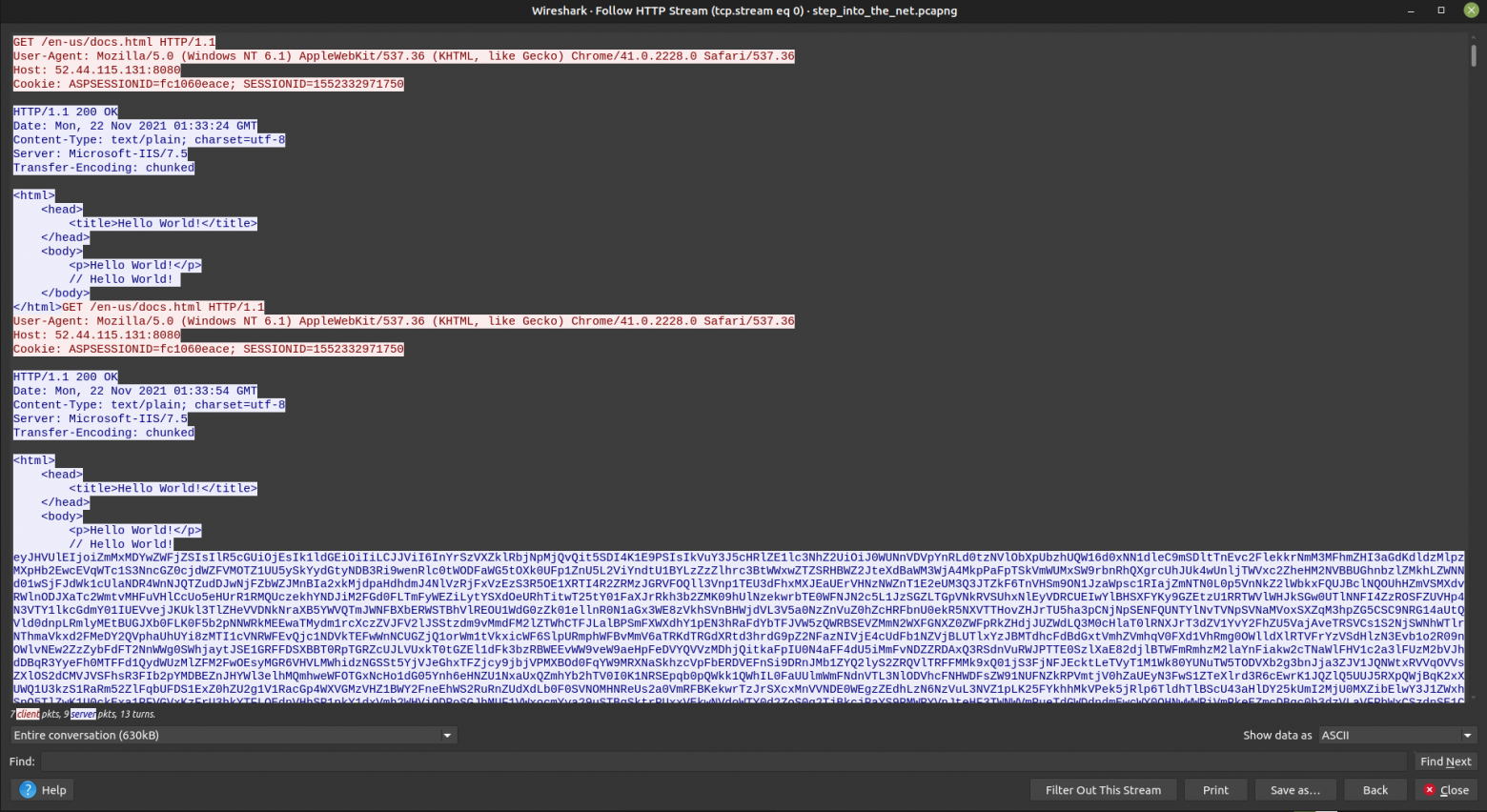
One detail immediately stands out: the entire session is 630Kb. It looks like a program was transferred here. I tried to find some useful data among the huge blocks of text, but they are most likely encrypted.
There is some useful information here, just captured packets showing downloading something encrypted.
This is a Windows dump file, so we will analyze it using WinDbg.
To parse a .NET program, you first need to install netext .
NET Login
As a grand finale, it's time to put all your forensics skills together. You have to work a little with Cryptography and Reverse Engineering, as well as with a large amount of Analysis.In this task, we took over the collection of intercepted packets and a dump of the process offered to you for consideration of the beacon.
In order to provide our leadership with the necessary clarity, we want to know specifically what actions the attackers took on this high-value machine (keep in mind - this is where the dump/captured packets are different from all previous tasks). Therefore, to recreate the picture of what happened, you will need to match the information in the intercepted packets and extract the necessary critical data from the memory dump.
Decision
Packet analysis
First, let's look at packet capture with wireshark to understand what we are dealing with.

Here I immediately notice two packages of interest to us:

GET /en-us/docs.htmlis of interest because immediately after we observe the sending of a large amount of data. That being said, I don't attach importance GET /latest/meta-data/instance-actionto , since it's something about an EC2 AWS server that was left behind by accident.

To see how the packages in question are involved in the entire session, use follow http stream.


One detail immediately stands out: the entire session is 630Kb. It looks like a program was transferred here. I tried to find some useful data among the huge blocks of text, but they are most likely encrypted.
There is some useful information here, just captured packets showing downloading something encrypted.
Dump analysis
This is a Windows dump file, so we will analyze it using WinDbg.

To parse a .NET program, you first need to install netext .
You must reply before you can see the hidden data contained here.
